
NJCCIC Archive
Security Notices
NJCCIC Weekly Bulletin | December 18, 2025
December 18, 2025
NJCCIC Alert | Phishing Campaign Impersonates Benefits Provider
October 30, 2025
NJCCIC Weekly Bulletin | September 18, 2025
September 18, 2025
NJCCIC Weekly Bulletin | September 11, 2025
September 11, 2025
NJCCIC Alert - Cybercriminals Impersonate NJ MVC in Recent SMS Text Phishing Messages
May 28. 2025
NJCCIC Weekly Bulletin - Fake CAPTCHA Malware Campaigns
March 20, 2025
NJCCIC Weekly Bulletin - Phishing Emails Impersonate IRS, Require Tax Payment
January 23, 2025
NJCCIC Weekly Bulletin - Credential and Card Harvesting Attack Impersonates American Express
December 12, 2024
NJCCIC Alert | Phishing Campaign Targets Students Seeking Financial Assistance
November 25, 2024
NJCCIC Weekly Bulletin | 404 Keylogger Snakes Its Way In
August 29, 2024
NJCCIC Weekly Bulletin | Pension Plan Help Scams
August 8, 2024
NJCCIC Weekly Bulletin | Observed Phishing Campaign Uses Adobe Acrobat
June 13, 2024
NJCCIC Weekly Bulletin | Recent Observed Iranian State-Sponsored Cyber Threat Group Activity
May 9, 2024
NJCCIC Weekly Bulletin | Continuation of SMS Text Phishing
March 28, 2024
NJCCIC Weekly Bulletin | Beware of Human Resources Phishing Emails
September 21, 2023
NJCCIC Alert | Maui Wildfire Charity Scams
August 24, 2023
NJCCIC Advisory | Employment Scams Continue
July, 27, 2023
NJCCIC Advisory | Fraudulent Claims Targeting Department of Labor Benefits Increase
July 20, 2023
NJCCIC Advisory | Threat Actors Continue to Impersonate Financial Institutions
June 29, 2023
NJCCIC Advisory | Multiple Vulnerabilities in Apple Products
June 22, 2023
Threat Actors Deliver Netflix-Themed SMiShing Text Messages
May 18, 2023
Fake PhishAlarm Installation Emails
May 11, 2023
Critical Patches Issued for Microsoft Products
May 10, 2023
Beware of Compliance Training Phishing Emails
April 20, 2023

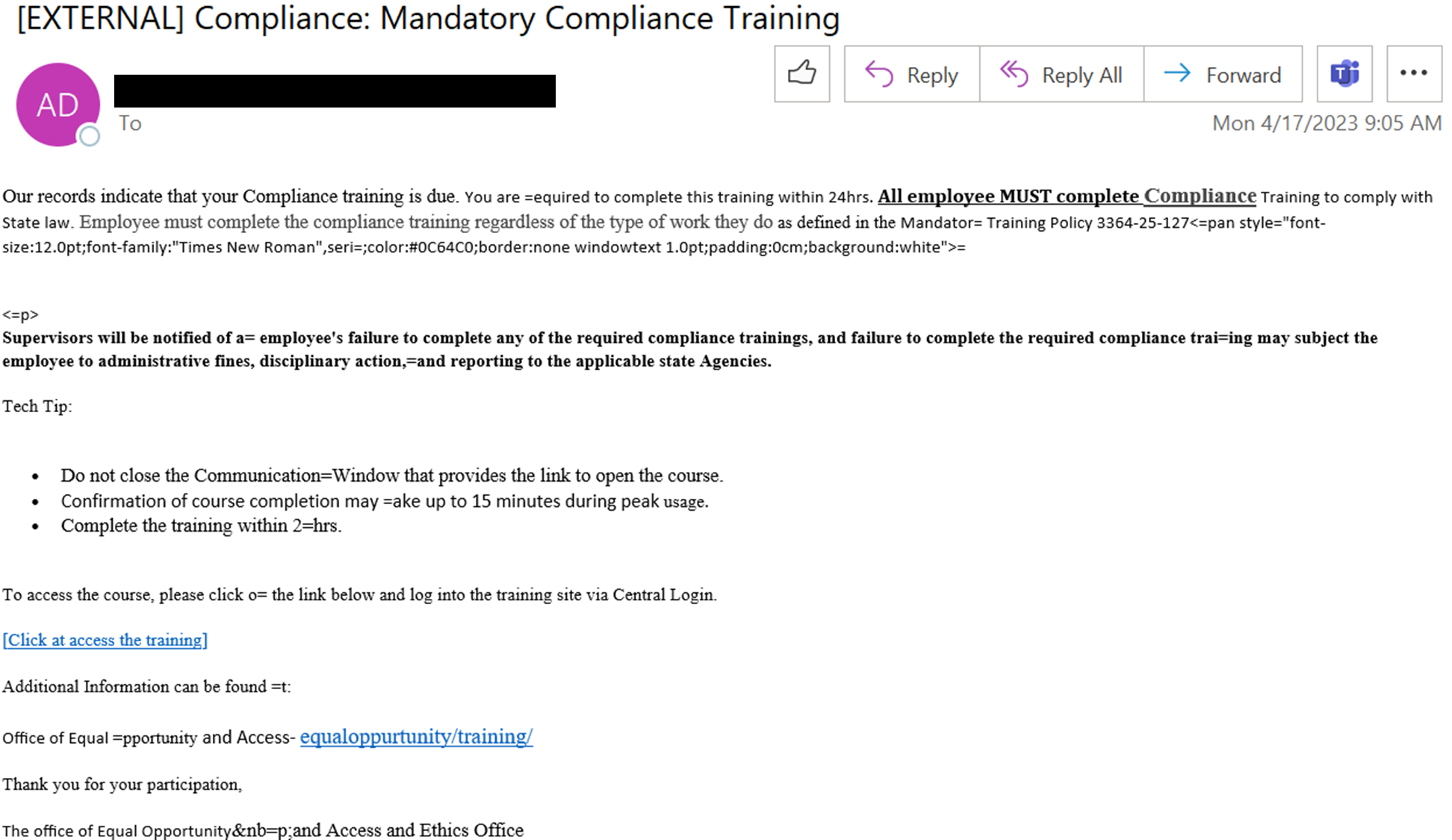
The NJCCIC received reports of a spearphishing campaign targeting the education subsector and masquerading as New Jersey State Compliance training. Observed activity correlates with blocked emails sent to New Jersey State employees and similar reports to State Fusion Centers across the United States. In one of the campaigns, a compromised email account of a school district employee was used to send fraudulent training compliance notifications. In attempts to appear legitimate and authoritative, the body of the email contained a signature block that included “The office of Equal Opportunity and Access and Ethics Office,” which is the incorrect New Jersey division title of The Office of Equal Employment Opportunity, Affirmative Action (EEO/AA).
The email contains additional red flags and typical verbiage to instill a sense of urgency and fear if the recipient does not comply with the requested action. The email text claims that the training must be completed within 24 hours, further stating that failure to complete the training may result in administrative fines, disciplinary action, and reporting to the applicable state agency. In one example, the email states that the non-descript employee must complete the training defined in the Mandatory Training Policy 3364-25-127, an Ohio administrative code. All included links directed the user to a now-defunct website, vvv[.]geopolisgis[.]gr/admin/video/subUrban_Planning/bid/login[.]php, limiting analysis of intent.
The NJCCIC advises against clicking on links in unexpected emails from unverified senders. Users are urged to confirm unusual requests to complete training with your organization’s compliance officer or HR representative. Additionally, users are encouraged to verify a website’s validity before entering account information and remain cautious even if messages claim to come from legitimate sources. If account credentials are submitted on a fraudulent website, users are advised to change their password, enable multi-factor authentication (MFA), and notify IT security personnel. Phishing emails and other malicious cyber activity can be reported to the NJCCIC and the FBI’s IC3.
Beware Zip attachments and Word documents from unknown senders
March 16, 2023
Social Engineering Scheme Impersonates NJ DOL
March 9, 2023
Phishing Email Impersonates Urgent Care, Requests Credentials to View File
December 15, 2022
Threat Actors Continue to Target Healthcare
November 10, 2022
MFA Prompt Bombing
September 22, 2022
Direct Deposit Scams Continue to Circulate
August 25, 2022
Document Lure Phishing Campaign Targets MFA Users
June 9, 2022
Recent Phishing Campaigns Employ Document Lures
June 2, 2022
Malicious Emails Targeting New Jersey Public Sector
March 11, 2022
Active Spearphishing Campaign Targeting NJ Public Employees
February 4, 2022
Document - Protecting Your myNewJersey Accounts
Facebook Messenger Scams and Schemes Targeting Cryptocurrency Holders
January 20, 2022
Multiple Vulnerabilities in Mozilla Firefox and Thunderbird
Could Allow for Arbitrary Code Execution
January 11, 2022
Multiple Vulnerabilities in Google Android OS Could Allow for Remote Code Execution
January 5, 2022
Evolving MirrorBlast Campaigns Attempt to Deliver FlawedGrace RAT
October 21, 2021
Vulnerability in Apple iOS and iPadOS
October 12, 2021
Security Alert Scam Spoofs Real Phone Number
September 30, 2021
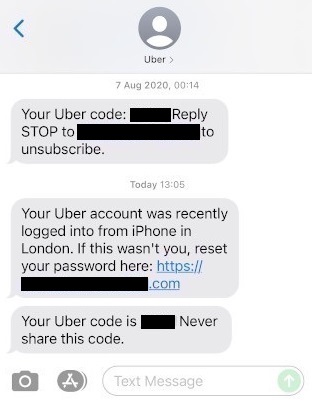
Image Source: Malwarebytes
Threat actors are spoofing real phones numbers of trusted entities to send convincing and urgent security alerts via SMS text messages. For example, a fraudulent Uber security alert is sent spoofing Uber’s real phone number and, therefore, appears in the same conversation thread as the previous, legitimate Uber messages. A link sent in the message includes the word “uber;” however, the domain name was only recently created, is hosted in a different country, and is not the official Uber domain name uber[.]com. To reset the password, the link directs the user to a fraudulent site containing convincing Uber branding and several pages to navigate through to verify one’s identity and enter both personal and financial information, including credit card and bank account details. Once information is entered, the user is redirected to the real Uber website without actually verifying their identity.
The NJCCIC recommends users and organizations educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to refrain from clicking links delivered in SMS text messages and, instead, navigate directly to the official corresponding website. If you are unsure of the legitimacy of the message, contact the sender via a separate means of communication—by phone or in person—before taking any action. Additional details of this scam can be found in the Malwarebytes blog post. For additional information and recommendations, please review the NJCCIC Products, Increase in SMS Text Phishing and Impersonation Scams.
Disaster Relief and Tragedy-Related Scams
September 2, 2021
Unemployment Insurance Fraud Increases
August 12, 2021
The Threat of Social Engineering
August 5, 2021
Navigating New Challenges This Academic School Year
Published September 2020
Credential Phishing Campaign
May 5, 2020
Multiple Vulnerabilities in Google Chrome Could Allow for Arbitrary Code Execution
January 21, 2020
Credential Phishing Campaign
November 19, 2019
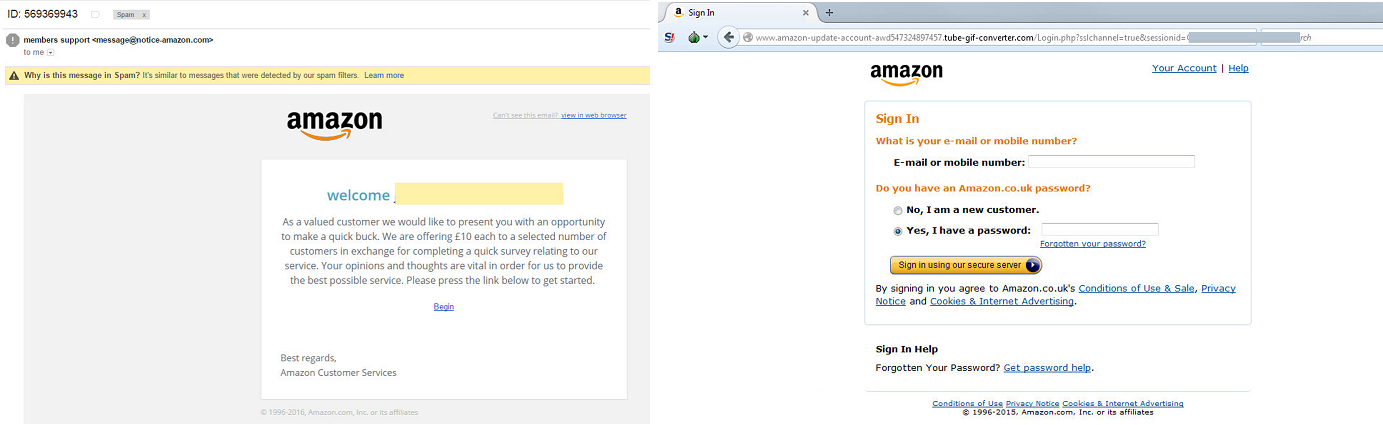
The NJCCIC continues to observe phishing campaigns attempting to steal credentials associated with online business services, including DocuSign, Amazon, and LinkedIn. These phishing emails contain HTML attachments or URLs leading to fraudulent account login pages designed to steal users’ login credentials. DocuSign phishing emails direct users to a site that prompts them to log in in order to view a protected document. Amazon and LinkedIn phishing emails request users to update their account information by directing them to fraudulent login pages. Stolen Amazon credentials can be used to make fraudulent purchases, while LinkedIn credentials can be used to access or contact a user’s connections. In all cases of credential theft, stolen passwords can be used in credential stuffing attacks that attempt to gain access to user accounts.
The NJCCIC recommends users refrain from clicking on links or opening attachments delivered with unexpected or unsolicited emails, including those from known senders. Users are advised to, instead, navigate to websites by manually typing the URL into the address bar of their browser. If credential compromise is suspected, users are advised to change credentials across all accounts that used the same login information and enable multi-factor authentication where available. Password reuse is highly discouraged.
Conversation Hijacking Scam
June 27, 2019
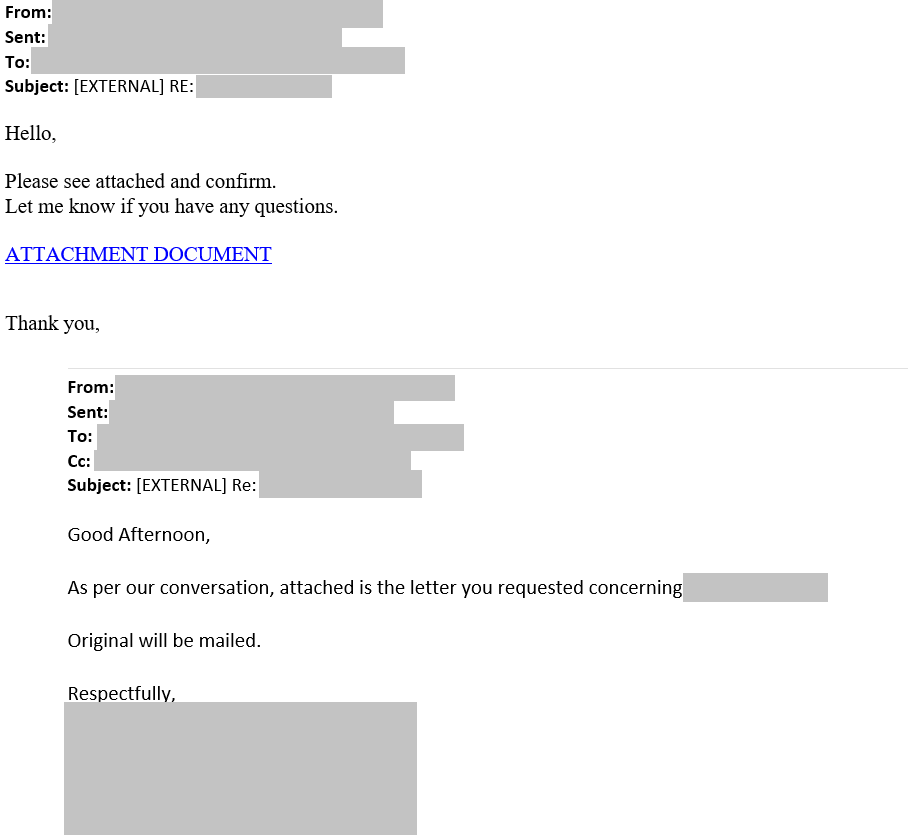
The NJCCIC has received reports of a conversation hijacking campaign distributed via spoofed email messages attempting to deliver theQbot banking trojan. These spoofed email messages appear to be replies to previous legitimate email conversations and contain OneDrive URLs linking to maliciousZIP files embedded with Visual Basic Script (VBScript). If executed, these files will download and install Qbot. Common subject lines associated with this campaign begin with “RE:” and include references to changes, updates, confirmations, and named individuals. Threat actors use highly-customized phishing techniques and realistic-looking email signatures to gain the target’s trust and trick them into downloading the malware. Qbot monitors the browsing activity of infected computers, records information from financial websites, and supports polymorphic capabilities, allowing it to self-mutate as it moves inside a network. Qbot may download files and exfiltrate other sensitive information including passwords from an infected system.
The NJCCIC recommends educating users about this and similar phishing threats, reminding them never to click on links or open attachments delivered in unexpected or unsolicited emails. Users are advised to run updated anti-virus/anti-malware programs on all devices and enable multi-factor authentication where available to prevent account compromise as a result of credential theft.
Office 365 Urgent Request Scam
May 27, 2019
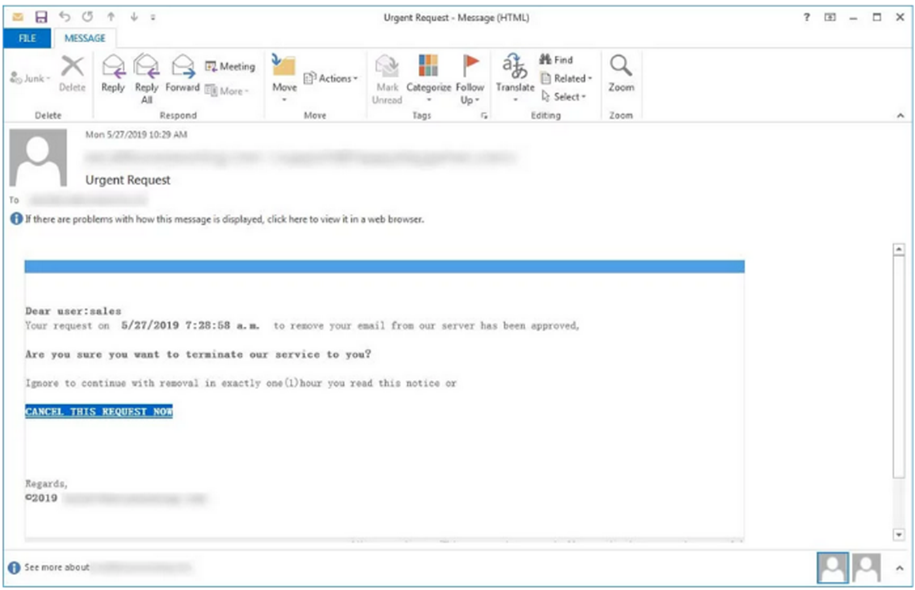
NJCCIC reports a new phishing campaign that claims to come from the “Office 365 Team”. The email warns the user that their account is going to be deleted unless the request is cancelled within the hour. This new campaign employs the old tactic of creating a sense of urgency to convince users to take risky actions, such as clicking on a link in an unexpected email. Once clicked, the link directs the user to a fraudulent Microsoft Office Support Account Update page that prompts the user to sign into their account in order to cancel the request. Once the user’s credentials are entered and submitted, they are sent to the threat actors and the user is redirected to a landing page with a “thanks!” message. The login and other landing pages were created using Excel Online. As always, if you have concerns with a message, report it to the Help Desk using spamFREEHUDSONCOUNTYCOMMUNITYCOLLEGE or call. If you have clicked on a link in this email, contact the Help Desk.
Contact Information
Information Technology ServicesJournal Square Campus
Patricia Clay
Associate Vice President for Technology and Chief Information Officer
70 Sip Avenue - 3rd Floor
Jersey City, NJ 07306(201) 360-4310
itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE
computerlabsFREEHUDSONCOUNTYCOMMUNITYCOLLEGE
North Hudson Campus
4800 John F. Kennedy Blvd - 3rd Floor
Union City, NJ 07087(201) 360-4309
itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE










































